Table of Contents
ToggleMany threats on Android spread through the ecosystem through existing apps, such as SMS apps and email clients. Google closely tracked a full week of activity and identified the most popular apps used to spread malware and potentially unwanted applications ( PUAs ).
Bitdefender has launched a new feature called Scam Alert through its Bitdefender Mobile Security for Android product which allows the security solution to examine incoming text messages and notifications. This is an opt-in feature, so only users who grant the necessary permissions can use it.
It can be strange to see a security solution focusing on SMS applications, as it seems that their use is decreasing year after year. The truth is that many of today’s cyber threats, such as the Flubot Trojan, are still carried out primarily through SMS. SMS applications are still widely used, especially by businesses that want to send information to users without relying on an internet connection.
Delivery services regularly use SMS messages to keep customers informed of the status of their packages, but Flubot operators use the same types of messages in many campaigns. And this is just one example among many.
Flubot is not the only player at stake
Flubot spreads its banking Trojans throughout the Android ecosystem, but there are many other threats, such as phishing, fraud, or simply potentially unwanted applications ( PUAs ). This last category is broad and includes apps that collect data they shouldn’t, abuse permissions to generate ad revenue, or trick users into making large payments, to name a few.
And, of course, there’s the relentless wave of spam that hits people every day. With Scam Alert, it is possible to intercept many of these threats before they become a problem. For example, when the user receives a notification from his email client containing a malicious web link (URL), Scam Alert immediately issues a warning.
The problem is that many apps use the notification system, and some abuse it outright. Google Chrome is a good example. We have all seen websites that request access to the notification system only to send countless annoying notifications.
PUAs and malware (Use early launch anti malware) are two different types of threats
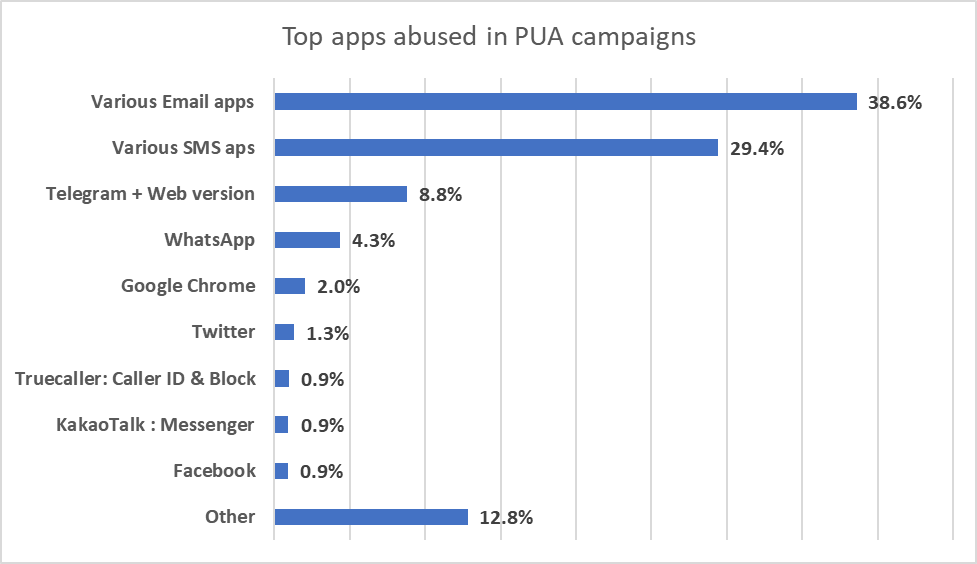
Most PUAs and spam are spread via email, it’s hardly surprising. Interestingly, SMS apps are also becoming a powerful infection vector, although it is not the first type of app we think of when it comes to PUAs or spam.
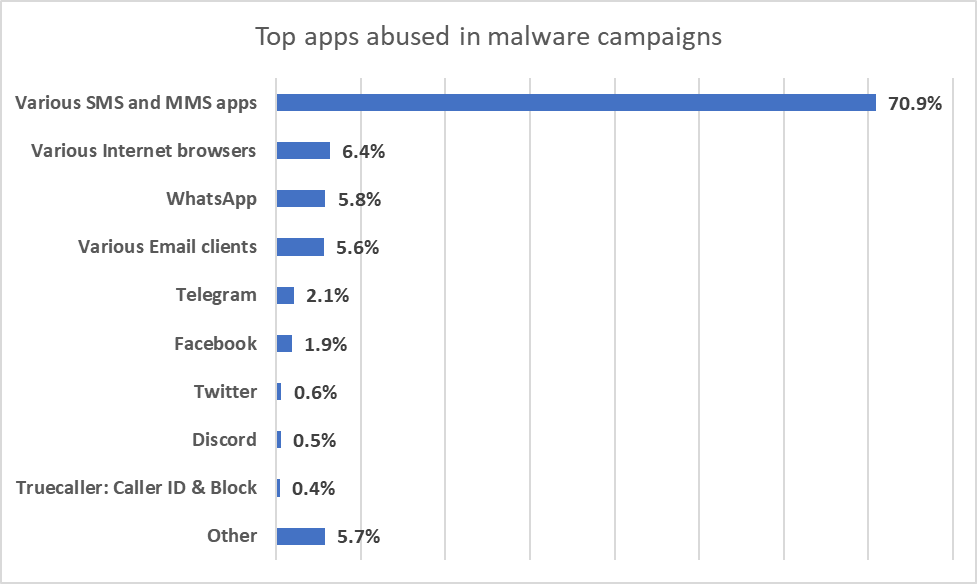
Malware (early launch anti malware), on the other hand, makes full use of SMS as a vector of infection, particularly because Flubot campaigns are proliferating rapidly in many parts of the world at the moment. It will be interesting to check this telemetry when Flubot is less active, but it has been going on for a few months, moving from country to country.
Scam Alert is the perfect tool for these types of threats, and it’s built into Bitdefender Mobile Security by default. It offers the right kind of protection at a time when people are inundated with malicious SMS messages containing malware ( early launch anti malware protection) and waves of fraud, spam, and unwanted apps that harass users every day.
The FBI advises businesses and individuals to be on guard against using virtual meeting platforms that are not normally used in your office environment. In addition, multi-factor authentication (double validation password/code received by sms or app) should be used systematically to better protect accounts.
In addition, the FBI offers guidance on verifying that links do not contain misspellings of a company’s domain name and are from the company or individual they claim to be from.
Additionally, the notice reminds users to refrain from emailing login credentials or personal information of any kind and to be wary of emails requesting personal information.
However, perhaps the best advice of all is that companies have a formal method for initiating funds transfers that allow staff to verify their veracity. Such processes should be explained across the company, and it should be clear that no one – not even the CEO of the company who might (or might not) be busy on a video call – can override it.

Usama is a Security blogger focusing on Cyber Security, Cloud Security, and IoT. He has worked as SR. Security Consultant for more than 4 years for industry-leading IT companies. Usama’s experience also includes working as a legal expert witness for Cyber management. He writes about industry technology trends and best practices. He incorporates his views and his many years of experience to provide unique technology advice for people that manage and support Cyber solutions.








